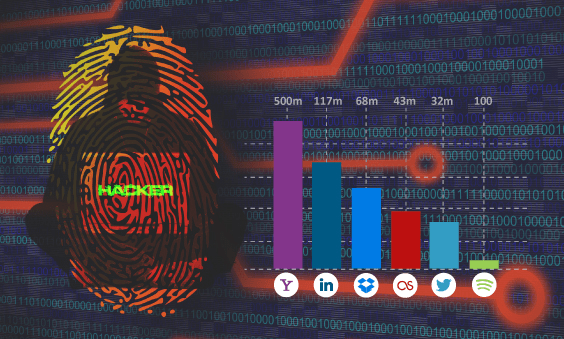
Passwords from popular platforms have been hacked! Is your company next?
Hackers break into a company’s internal network and attempt to get a copy of the password database. The cost and......
What to look for in an anti-counterfeiting and anti-diversion solution?
According to an estimate issued by International Chamber of Commerce (ICC). Besides, brands suffer from negative impacts such as brand image damage and loss of customer confidence due to......
An Unguarded Front Gate
2014 Data Breach Investigation Report from Verizon reported that the number one way hackers are gaining access to information on computer networks continues to be the......
Before IoT, let’s talk about rigorous application security
The use of web applications in the enterprise has grown exponentially in the last decade. This will likely continue into the next decade, driven by trends such as the Internet of Things (IoT).
Authentication methods keeping pace with BYOD, cloud
The consumerization of IT and bring your own device (BYOD) initiatives in the workplace are challenging IT leaders to deliver secure mobility without spoiling users’ mobile experience.......
How smart financial institutions develop versatile authentication
The survey of 725 senior financial services leaders in Australia, Hong Kong, Japan, the UAE, the UK and Singapore also showed that IT security is now more likely to get......