Imagine a world where today’s strongest encryption systems are cracked in seconds. With the rapid advancements in quantum computing, this is no longer a distant possibility—it’s an impending reality.
Quantum computing holds immense promise for solving complex problems, but it also introduces new risks to cybersecurity. At i-Sprint, we’re staying ahead of the curve by integrating quantum-safe IAM solutions to protect your data in this evolving landscape.
What is Quantum Computing and How Does It Work?
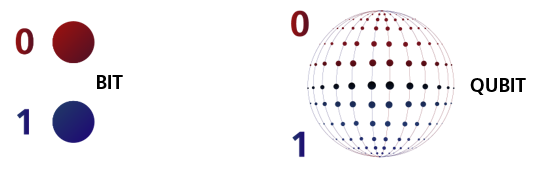
Quantum computing is fundamentally different from classical computing. Instead of bits that are either 0 or 1, quantum computers use qubits, which can exist in multiple states simultaneously thanks to the principles of superposition and entanglement.
This means quantum computers can perform calculations at unprecedented speeds, solving problems that classical computers would take years—or even millennia—to process.
Classical Computers


Quantum Computers


While this power has revolutionary potential in fields like drug discovery and logistics optimization, it also poses a serious threat to widely used cryptographic systems such as Public Key Cryptography like RSA. These systems rely on the difficulty of solving certain mathematical problems, like factoring large numbers—problems quantum computers can solve with ease.
Why Is Quantum Computing a Problem for Cybersecurity?
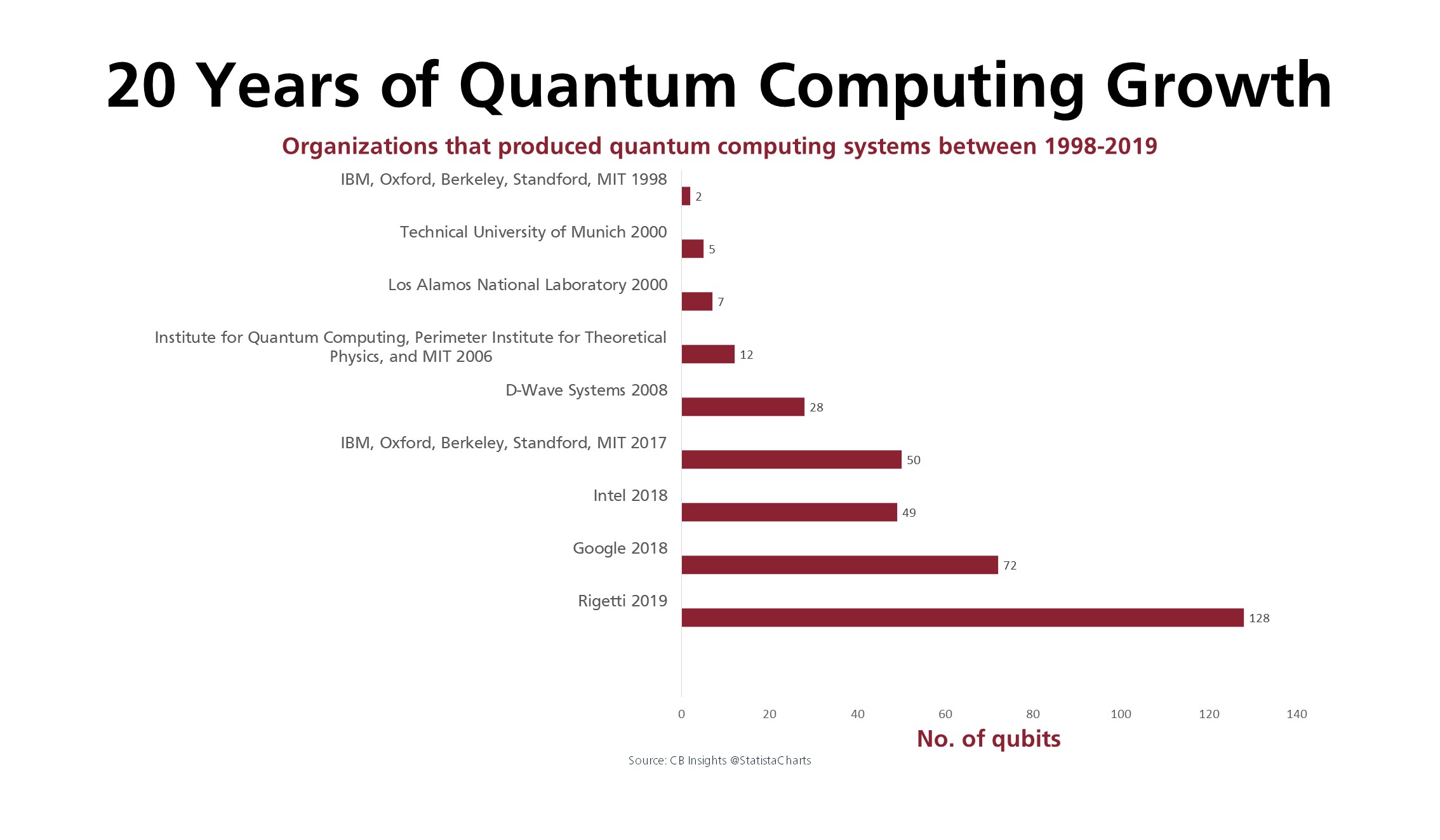
Rapid Advances in Quantum Computing
Quantum computing technology has grown exponentially in recent decades. Between 1998 and 2019, leading organizations made significant progress in quantum systems, culminating in a landmark achievement in 2022 when IBM launched Osprey, a quantum computer with an impressive 433 qubits.
Breaking Encryption Barriers
Today’s encryption standards, such as RSA-2048 and AES-256, are robust against classical threats. However, cybercriminals can potentially exploit quantum computers’ power to break these encryptions in minutes. This could render modern encryption techniques obsolete, opening the door for them to exploit sensitive data.
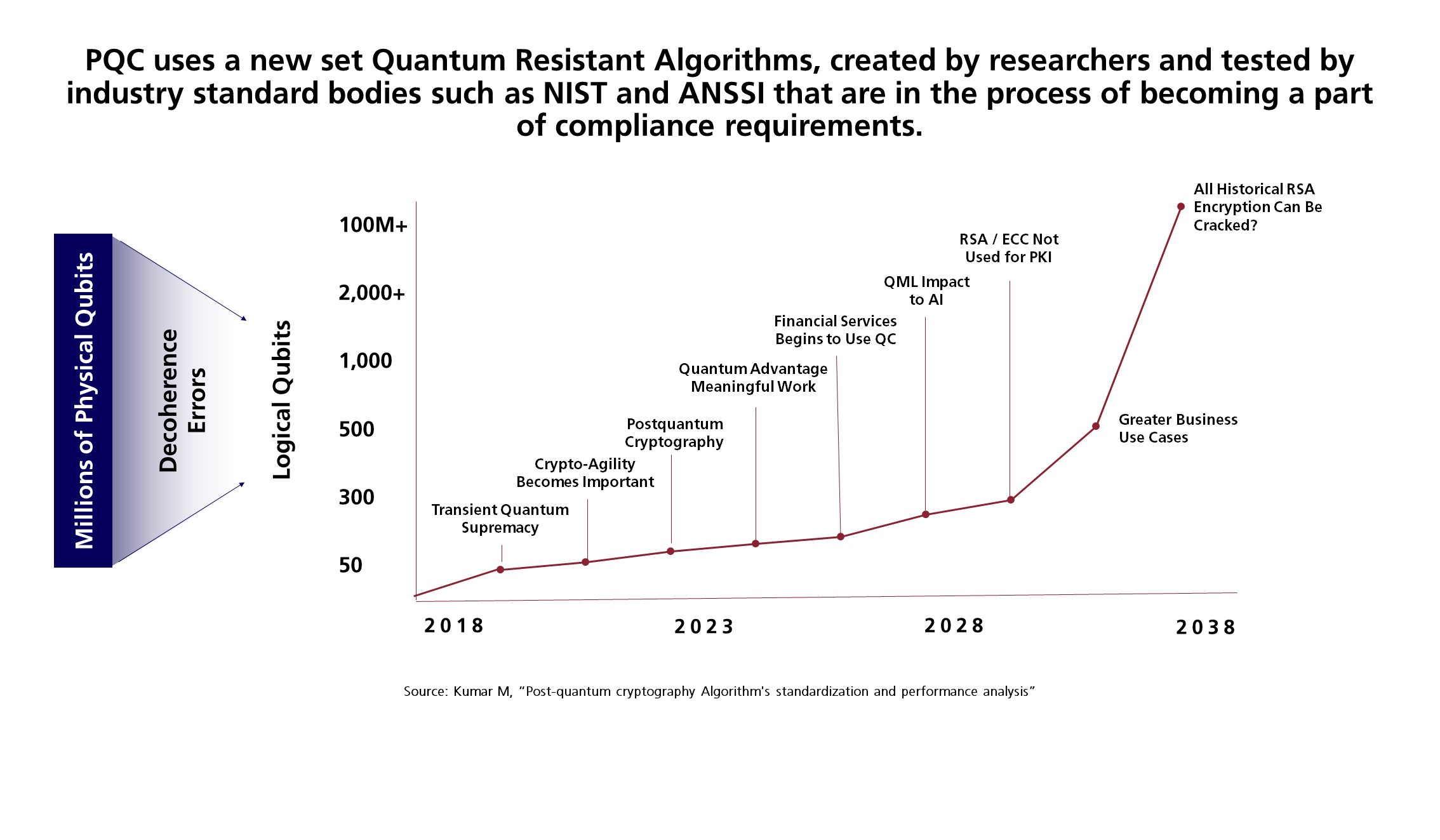
As quantum computing capabilities grow exponentially, Gartner predicts that traditional cryptographic methods like RSA and ECC will no longer be viable for public key infrastructure (PKI) by 2029. Alarmingly, by 2034, quantum computers are projected to crack all historical RSA encryption, exposing decades of sensitive data to potential compromise. This rapid advancement highlights why organizations must act now to adopt post-quantum cryptography and safeguard their systems against future threats.
The Real Threat: “Harvest Now, Decrypt Later”
The rise of quantum computing has also introduced a new kind of cyber threat: attackers could steal encrypted data today and decrypt it years later when quantum systems are fully developed. This is known as the “Harvest Now, Decrypt Later” strategy.
Gartner emphasizes the urgency of addressing this risk:
“Failure to migrate to new quantum-safe cryptographic algorithms can leave application and data security at risk of compromise. Security and risk management leaders must prepare for ‘harvest now, decrypt later’ attacks by merging cryptographic upkeep with DevSecOps.”
— Gartner, Preparing for the Quantum World With Crypto-Agility, 2022
This threat is particularly alarming for industries like finance, healthcare, and government, where long-term data confidentiality is critical.
The Solution: Post-Quantum Cryptography (PQC)
To combat these emerging threats, Post-Quantum Cryptography (PQC) has been developed. Unlike traditional cryptographic methods, PQC algorithms are designed to withstand attacks from both classical and quantum computers.
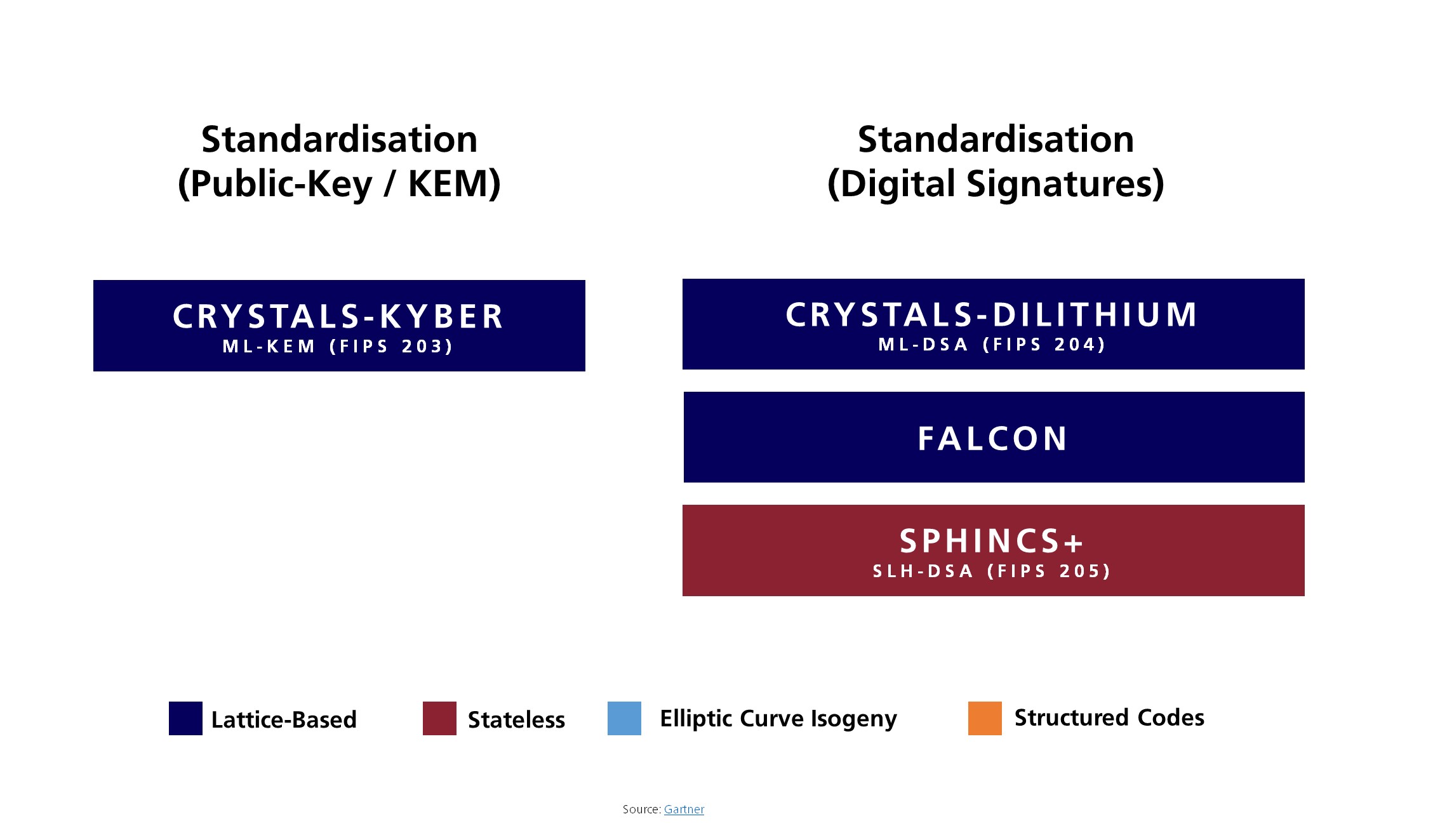
Recognizing the urgency of quantum threats, NIST (National Institute of Standards and Technology) began the standardization process for PQC algorithms in 2016. This initiative aims to identify and formalize cryptographic methods that can protect against quantum attacks.
One of the finalized post-quantum encryption standards from NIST’s program is CRYSTALS-Kyber (renamed ML-KEM), a lattice-based encryption algorithm known for its efficiency and resistance to both classical and quantum threats.
Key Benefits of PQC:
- 1Long-Term Data Security: Protects sensitive information from quantum decryption.
- 2
Regulatory Compliance: Meets emerging standards, such as those set by MAS.
- 3
Future-Proof Solutions: Ensures resilience in the face of advancing quantum threats.
By adopting PQC now, organizations can proactively safeguard their systems and maintain trust in an increasingly uncertain digital landscape.
MAS Advisory on Quantum-Safe Solutions
Recognizing the urgency of quantum threats, the Monetary Authority of Singapore (MAS) has issued an advisory encouraging financial institutions to adopt quantum-safe technologies. This move underscores the critical need for organizations to act now.
At i-Sprint, we align our solutions with MAS’s guidance, integrating quantum-safe IAM technologies to protect your organization while ensuring compliance with regulatory expectations.
Whether you’re in finance, healthcare, or any other industry handling sensitive data, our quantum-safe IAM solutions provide the resilience you need to stay ahead of evolving threats.
The quantum era represents both an opportunity and a challenge. Organizations that act now to implement quantum-safe solutions will not only safeguard their data but also stay ahead of evolving threats and regulatory requirements.
At i-Sprint, we are committed to helping you future-proof your cybersecurity framework with innovative, compliant, and quantum-safe IAM solutions.
Don’t wait until it’s too late—secure your enterprise’s data today with i-Sprint.