
Hackers Are Exploiting Frida. Is Your Mobile App at Risk?
Frida is a powerful tool for mobile app security testing, used by developers, security researchers, and reverse engineers to inspect and modify app behavior. However, the same capabilities that make Frida useful also make it a weapon for cybercriminals. Hackers manipulate Frida to inject malicious code, bypass security measures, and extract sensitive data all without detection.
As hacking techniques grow more sophisticated, traditional defenses like memory scanning and static threat monitoring are no longer enough. Developers need advanced, proactive security measures to protect app integrity and user data.
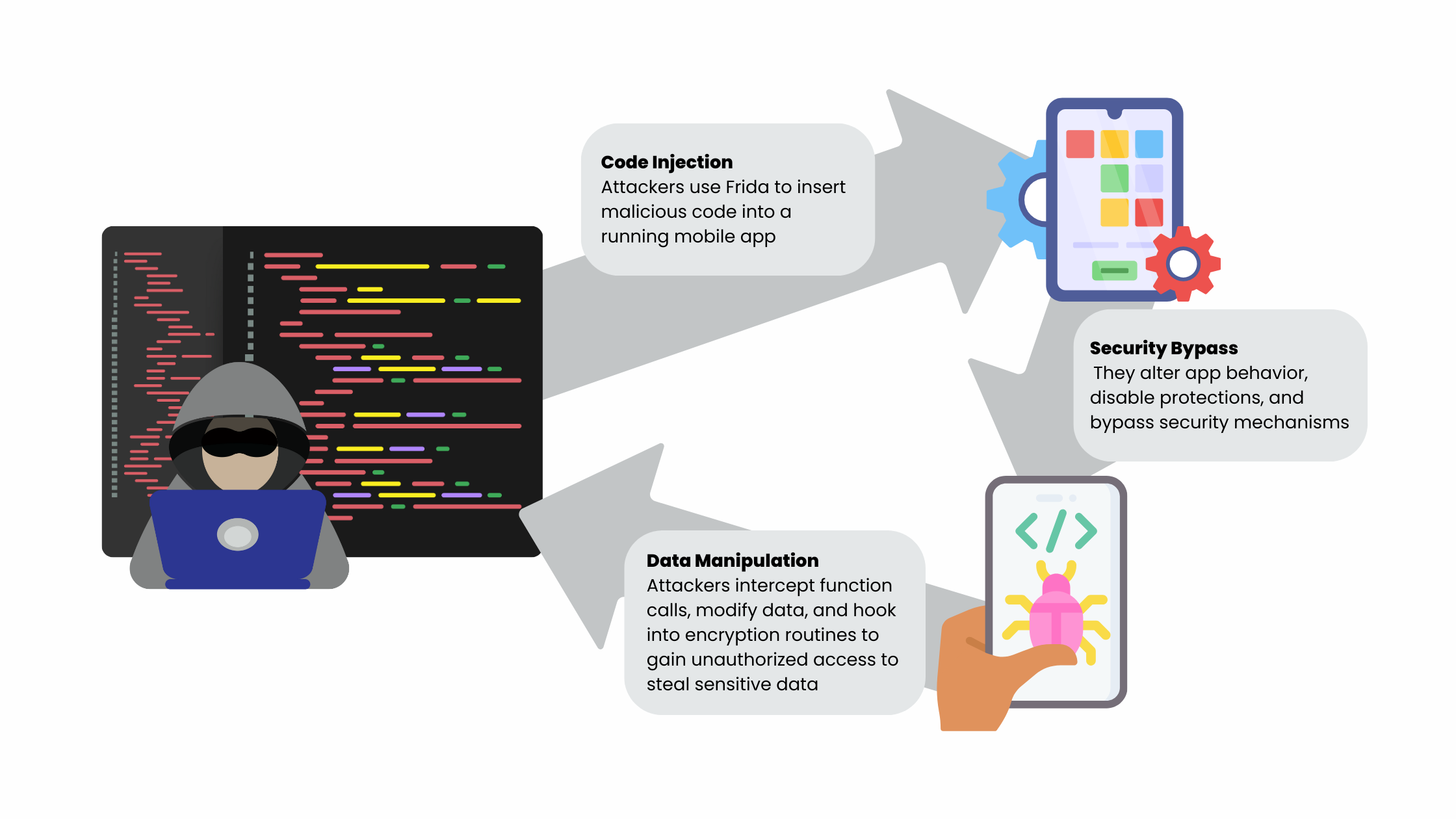

Hackers frequently modify Frida to evade detection, allowing them to:
Is your app equipped to defend against these growing threats?
YESSafe AppProtect+ Suite: A Powerful Defense Against Frida-Based Attacks
As cyber threats evolve, app developers need a security solution that does not just detect threats but actively prevents them. YESSafe AppProtect+ provides multi-layered protection against Frida and other runtime threats, ensuring your mobile applications remain secure
Key Features Protecting Against Frida-Based Attacks
Why Choose YESSafe AppProtect+?
Over 97% of top Android apps remain vulnerable to runtime threats like Frida, exposing users to data theft, fraud, and privacy breaches. YESSafe AppProtect+ provides real-time protection against these threats, ensuring your mobile application stays secure against both known and emerging attacks.
Don’t wait until your app is compromised. Contact us today to see how YESSafe AppProtect+ can fortify your mobile security!
