Product Introduction
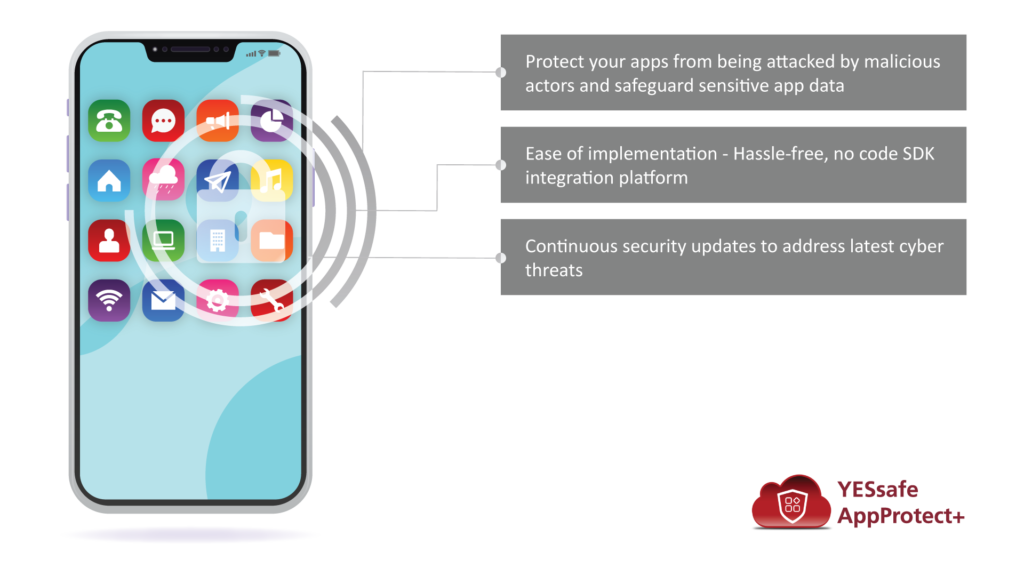


YESsafe AppProtect+ detects and protects the mobile app from threats, such as reverse-engineering, tampering, code-injection and more. In an insecure OS environment, apps integrated with YESsafe AppProtect+ have rooted and jailbreak detection mechanisms that allow a mobile app to operate securely without compromising the app’s integrity and confidentiality.
Protecting apps even in the absence of an internet connection or without an updated virus database, AppProtect+ protects mobile apps against static and dynamic attacks (e.g. repackaging, source code modification), and respond by taking necessary measures when real-time attacks are detected during runtime.
Moreover, AppProtect+ is EMVCo SBMP certified. An EMVCo certified app solution ensures that mobile apps can withstand real-time threats and attacks.
Runtime App Self-Protection (RASP)
- AppProtect+ isolates applications from the runtime environment to proactively scan and protect mobile apps against malicious attacks, allowing apps to run securely even on rooted/ jailbreak devices. E.g. upon detection of the presence of an untrusted screen reader, AppProtect+ blocks the screen reader from receiving data from the protected app.
- The uniqueness of AppProtect+ lies in the ability to detect risks even in the absence of an internet connection. AppProtect+ can avoid possible risks caused by a desynchronized database.



Core Functions
YESsafe AppProtect+ responds promptly to any risk detected on the client side. Fulfilling app protection, risk detection and respond actions requirements, providing the complete app protection cycle.
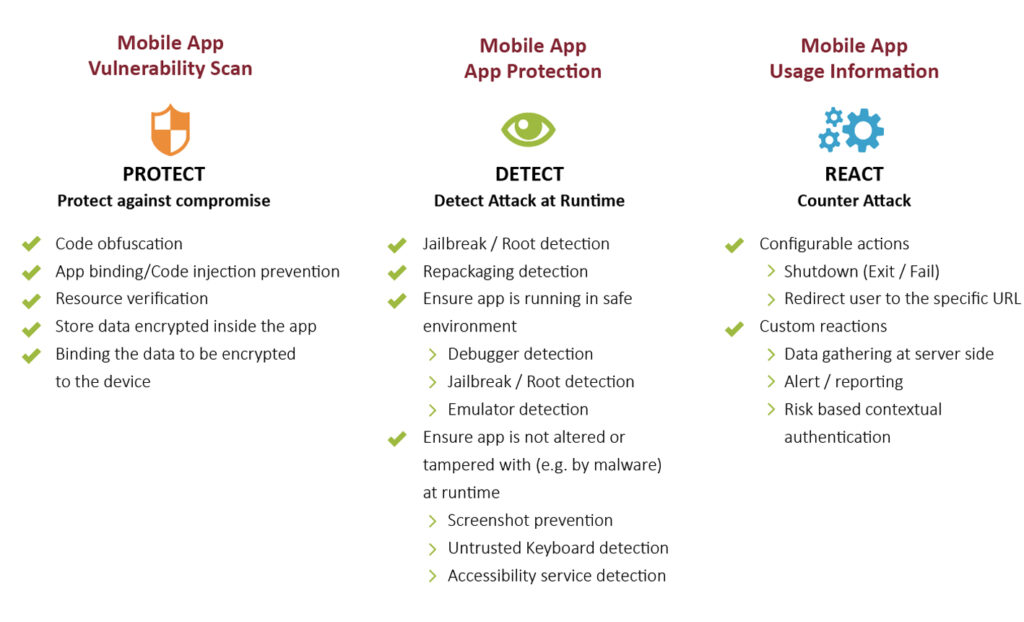


All-Round Protection



Code Injection
- Prevent hackers from modifying code and changing the course of execution, resulting in data loss or even a complete host takeover



App Repackaging
- Prevent repackaging of applications and imposter from publishing repackaged apps in official app stores



Emulators & Debuggers
- Protect applications from attackers using emulators and debuggers to intercept data before it is encrypted.



Reverse Engineering
- Multiple layers of security check to hinder any reverse engineering attempts



Jailbreak/ Rooted Devices
- Automated detection of jailbroken and rooted devices, ensuring app is executed the way you configure it to be




