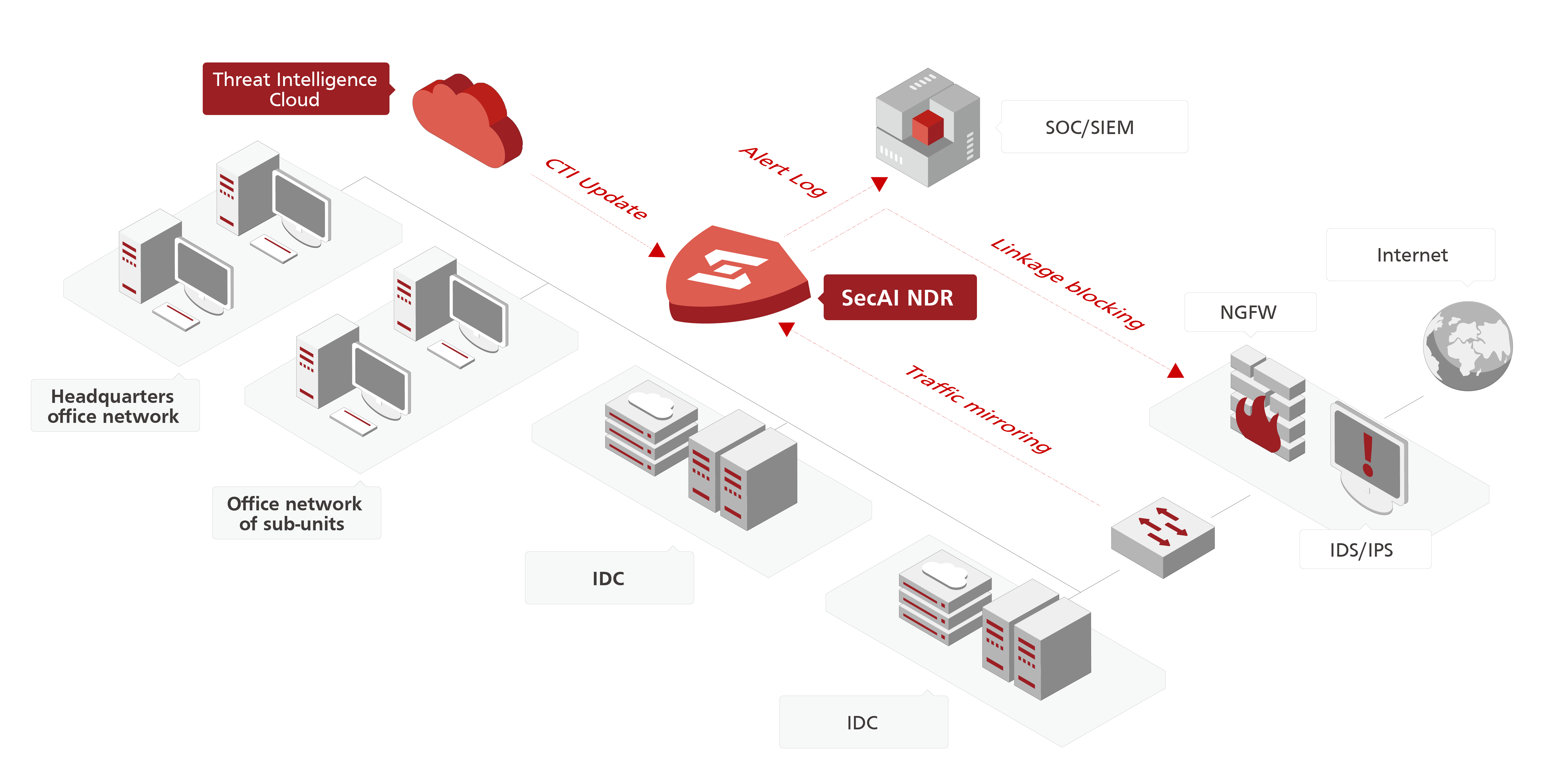
Network Detection and Response (NDR)
NDR provides the most effective network security capabilities with high-fidelity
detection on sophisticated attacks and automated response with a low false positive
rate of less than 0.03% and a high zero-day detection rate of over 81%