2FA: Strengthening User Access Control
Strengthening Authentication without Sacrificing User Experience
Two-factor authentication (2FA) – the need of two methods of authentication factors to verify user’s identity. 2FA aims to strengthen user’s access security, preventing attackers from exploiting weak login credentials with the introduction of an additional authentication factor. These factors can include:
- Something you know – e.g. password, PINs
- Something you have – e.g. smartphone, OTP token
- Something you are – e.g. fingerprint, biometrics
How 2FA works?
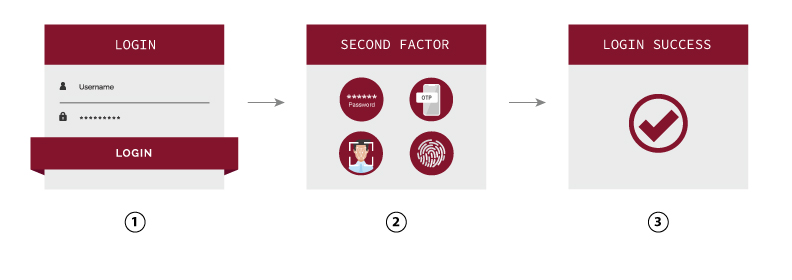
i-Sprint Two-Factor Authentication Solution
*i-Sprint 2FA solution allows integration with SingPass/ CorpPass (SPCP) using SAML 2.0 protocol. It also supports Assurity OneKey Token using the Singapore Technical Reference TR-29 protocol.
Interested in Learning More?
Connect with a specialist to address your queries and find solutions tailored to your needs.




